Unlocking the AWS Maze: Understanding Security Groups, NACLs and Traffic Flow Inside EC2 Instances
Case study:
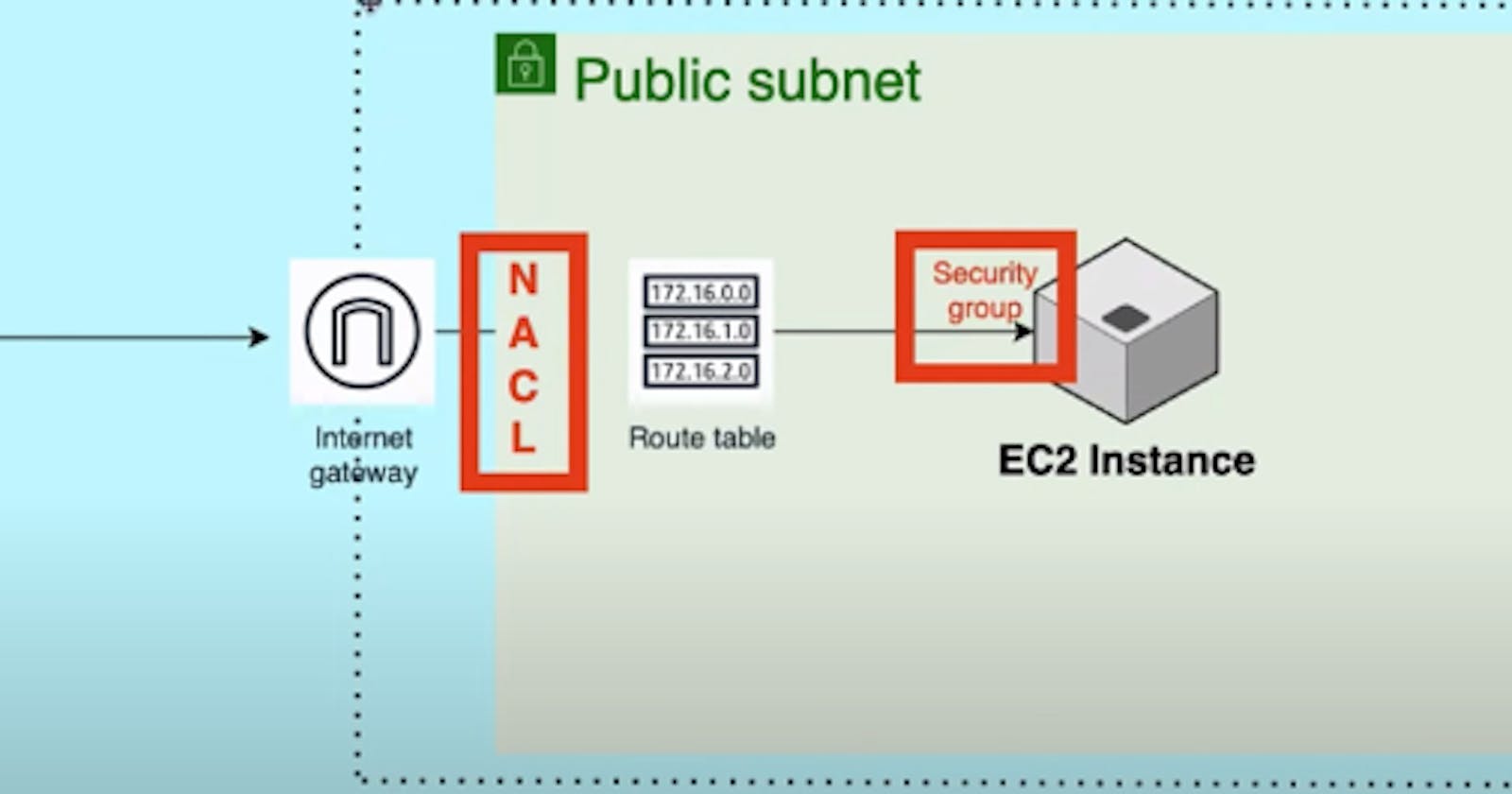
In this blog we will See the different cases with security group ,NACL configuration. In addition, we will understand how traffic flows application inside ec2 instance. For example, we will see cases like allow in security group and blocking in NACL, allow in NACL and blocking in security group and so on.
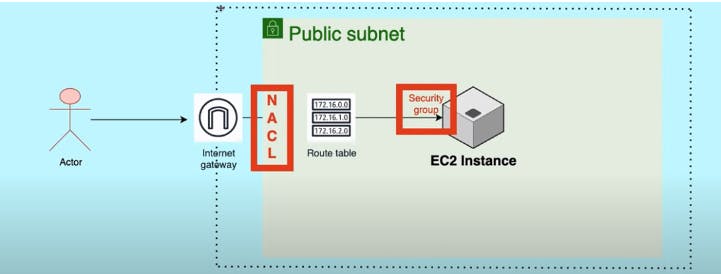
Pre-requisites:
1)Create a VPC(by using vpc and more).
Output: In aws console, VPC will be displayed as below.
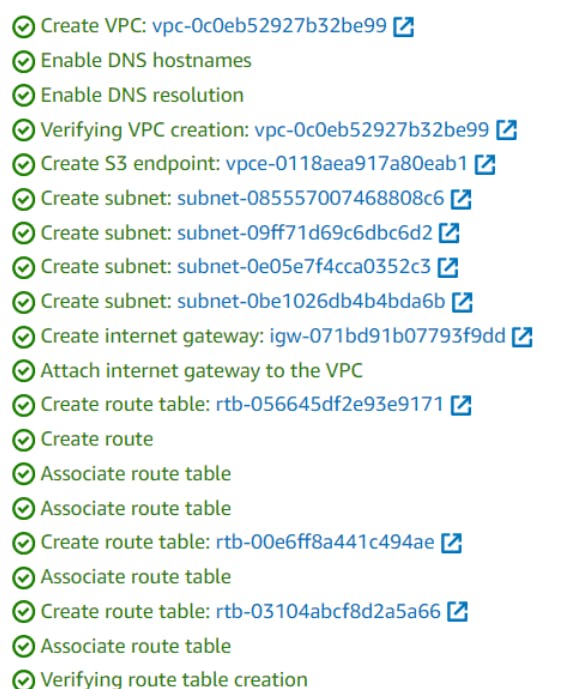
In the above configuration we can see that there are two public subnets and two private subnets. Also, two route tables as well as internet gateway connection which are required for this case study.
2)creating a EC2 instance with below configuration.
2.1)Instance should be created in public subnet in one availability zone only.
2.2)Auto-assign-enabled
2.3)Let AWS will create a security group and make our test cases .
Output: In AWS Console instance(demo python server) will be displayed as below.
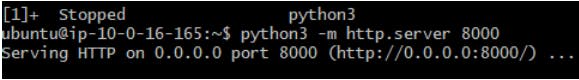
3)Now run simple http server on python on ec2 with port 8000.
Test Cases for the Case Study:
Case-1:Ideally we can access the server on port 8000.
->If we run http://publicip:8000 on browser.
Output : Application is not accessing as below.
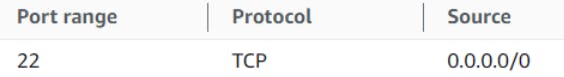
Reason: In default SecurityGroup which is attached to ec2 instance, only ssh (port 22) traffic is allowed. Even if it is not allowed we cannot login to ec2instance.
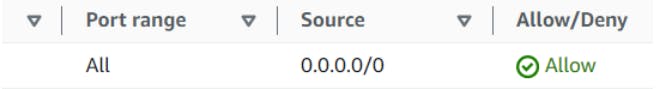
Nacl: we can see allow all , so , all traffic is allowed in order of priority with least number.
Conclusion: From the above configuration we can see that Although Nacl is allowed, security group is blocking the traffic.
Case - 2: Unblock the security group from case-1.
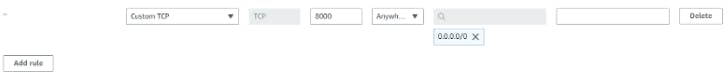
->We are allowing port 8000 in which our server is present. Custom TCP means we can allowing custom port 8000 of TCP. Also, we are allowing port 8000 from any ip address.
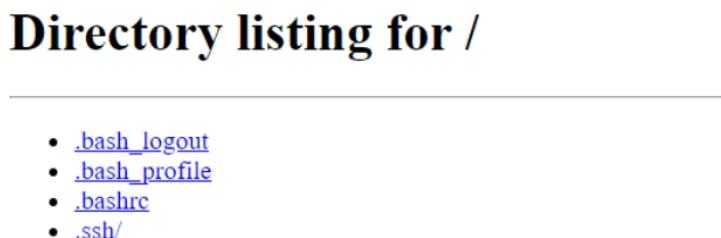
Output: After refresh the page, we can see the output running a simple http server which listing out the directories in the folder.
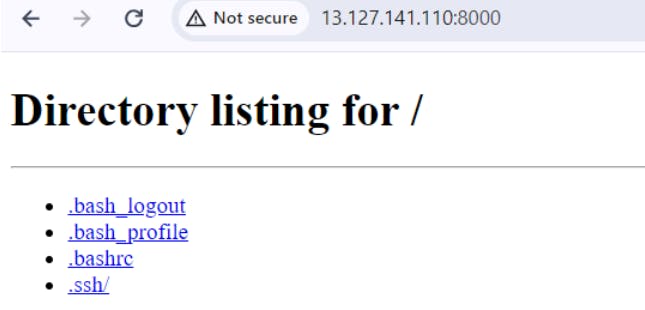
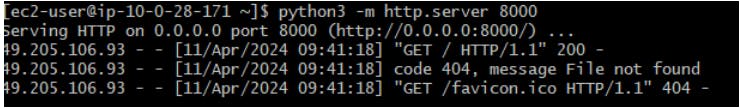
Validated the request out from the 200 response.
Case-3:Blocking the port 8000 in NACL level configuration. Assume it is an organization level standard.
->Edit the inbound rules by adding the new rule. Anything coming from internet to access port 8000 is deny.
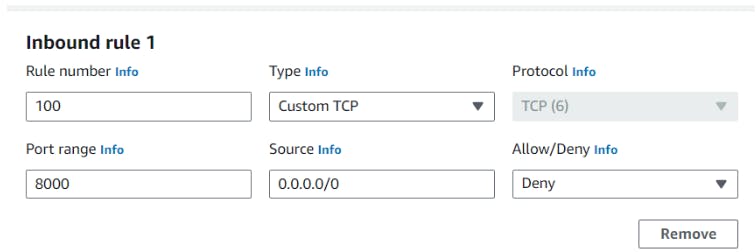
Testing: Copy paste the url in browser.
Output: Site cannot be reached.
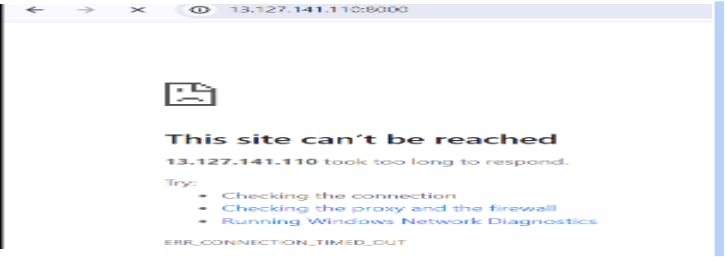
Conclusion: organization has blocked specific ip range in nacl. Hence it will block the entire subnet . we cannot access the resources like ec2 or any other associated with in the subnet.
Case-4:
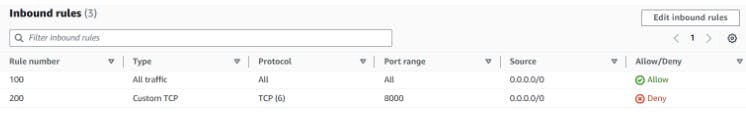
->Again allow all traffic for 100 rule number as seen below.
->Also, allow 8000 port for allow traffic and deny with rule number 200.
Testing: Copy paste the url in browser.
Output: Site is reaching again.
Conclusion:Although we have deny rule .Aws will verify first lowest number which is 100 . since rule 100 which has allow all traffic and it checks the security group which has custom tcp port 8000.
Other cases:
->Block the ip address coming from specific address.
->creating the security groups in private subnets and load balancers and many more.